A Unified Purple Teaming Approach on WINRM Investigation and Detection
OVERVIEW
In this blog we will be discussing the unified Purple Teaming approach for Active Directory attack and detection.
In general Active Directory (AD) acts as a crucial component of many organization infrastructure and plays a fundamental role in network management and security. Let us perform a red team simulation over an AD infrastructure and investigate the same using multiple blue team solutions.
The Approach:
As we aware that the purple teaming is a collaborative effort aimed at improving organization security by simulating and assessing various detection and defensive controls,
The team CWL has been dedicatedly working on the building a real world purple team infrastructure, where the participants can be performed and simulate 30+ real world attack simulation & detection
The Architecture:
| S.No | Machine Name | IP | User | Password |
| 1 | DC | 10.3.0.2 | NA | NA |
| 2 | DJ1 | 10.3.0.12 | Emp1 | Employee@1 |
Blue Team Solution
| S.No | Service | User |
| 1 | SIEM | ELK + Wazuh |
| 2 | Real-Time Monitoring | OS-Query |
| 3 | Network Monitoring | Akrim Moloch |
The below mentioned is our pre-configure infrastructure for our purple team simulation.
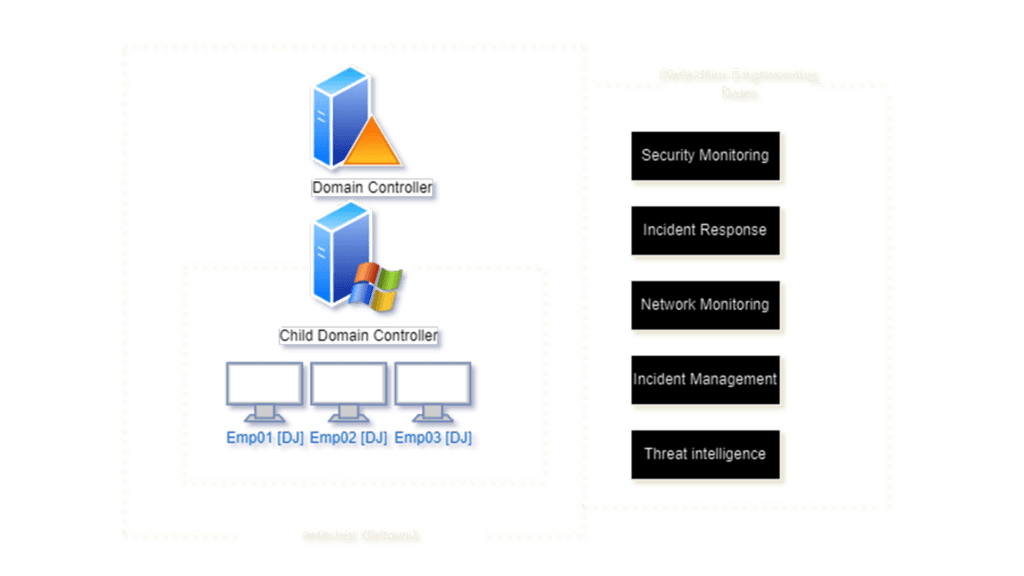
For deploying and developing Purple Teaming Infrastructure check out our Purple Teaming Fundamentals Community Edition mini-course.
Planning and Preparation
Red Team Objective
In our lab setup the goal of the Red Team scenario is to get an initial foothold to Active Directory network using WinRM [Windows Remote Management]. We will be actively attempt to exploit the open service to gain access with the target system.
Blue Team Exercise
The primary objective of the Blue Team scenario is to conduct an investigation and create a baseline detection rule for WinRM Based Initial Access. Participants will focus on detecting and responding to potential attacks, enhancing their incident response skills and strengthening the overall security posture.
Breach & Attack Simulation
- Traditional AD assessment begins with scanning the target machine using various tools such as NMAP etc.
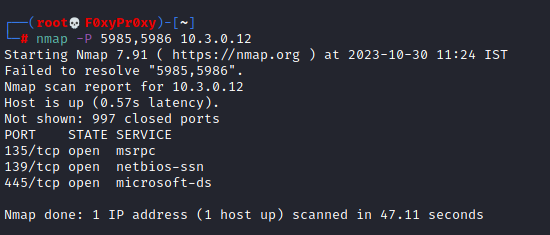
- If in case we observe that the port 5985 was exposed publicly. This can be targeted to execute remote code execution via remote system.
- As we determined the target port 5985 is associated with the Windows Remote Management service, also known as WinRM. It’s used for remote management and administration of Windows-based systems, often in enterprise environments.
- We are assuming that we have the enterprise user credentials. Initial Access can be achieved via “evil-winrm”
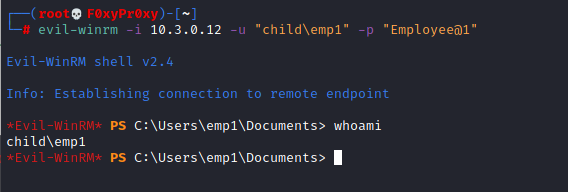
//evil-winrm is a tool used in penetration testing for remotely managing Windows systems, It is generally used to establishing remote PowerShell sessions over vulnerable Windows machines

As per our Red Team Simulation we have successfully accessed the WinRM Server.
Detection & Investigation:
Generally Investigating a WINRM based attack is a complex process which requires multiple correlations and confirmations.
Initial step of investigation required to have a basic understanding of WINRM.
- Evil-WinRM generally targets systems over the specified port (usually 5985 for HTTP or 5986for HTTPS).
- Next attempt is to authenticate to the target Windows system using the provided credentials (username and password or other authentication methods).
- After establishing connectivity with the target it initiates the Remote PowerShell session with the target system to maintain a stable connection.
Our first step of investigation begins by investigating the powershell activity with a warning event over the SIEM Solutions.
data.win.system.providerName: Microsoft-Windows-PowerShell and data.win.system.severityValue:"WARNING"
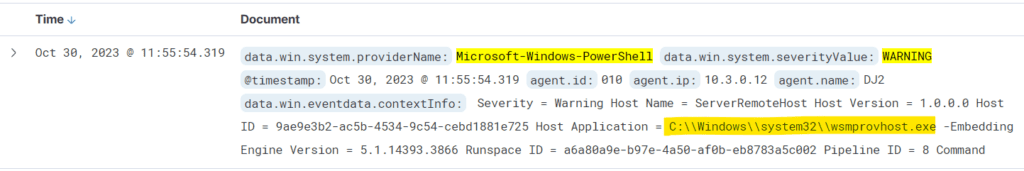
Note: PowerShell logs can also be viewed using the Windows Event Viewer. The event log is located in the Event Viewer → Application and Services Logs → Microsoft → Windows →PowerShell

From the above result we observed a powershell event with the severity Value “WARNING“, has been invoked by the process C:\Windows\system32\wsmprovhost.exe -Embedding.
Our next stage of investigation is to determine the root cause for the powershell execution using Osquery,
Note: Osquery is an open-source cybersecurity tool that provides a powerful and versatile means of monitoring and querying endpoints and servers in real-time
The first step of the osquery investigation is to determine the PID of the process wsmprovhost.exe
Select * from processess where name=’wsmprovhost.exe’

After determining the PID of the process wsmprovhost.exe, the next step identify the actual process execution flow
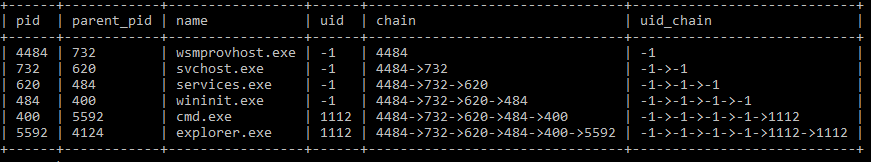
As per the above observation there is a high possibility that it might be compromised and communicating to the external network to confirm the activity, it is recommended to check the network communication of the detected host machine.
Note: Windows Remote Management (WinRM) is the Microsoft implementation of the WS-Management protocol,
Remote PowerShell sessions often execute commands within their own context, and the remote machine might not store the full command history in the same way as a local PowerShell session. To confirm the wsmprovhost.exe activity it is recommended to check the network traffic observed over the port 5985.
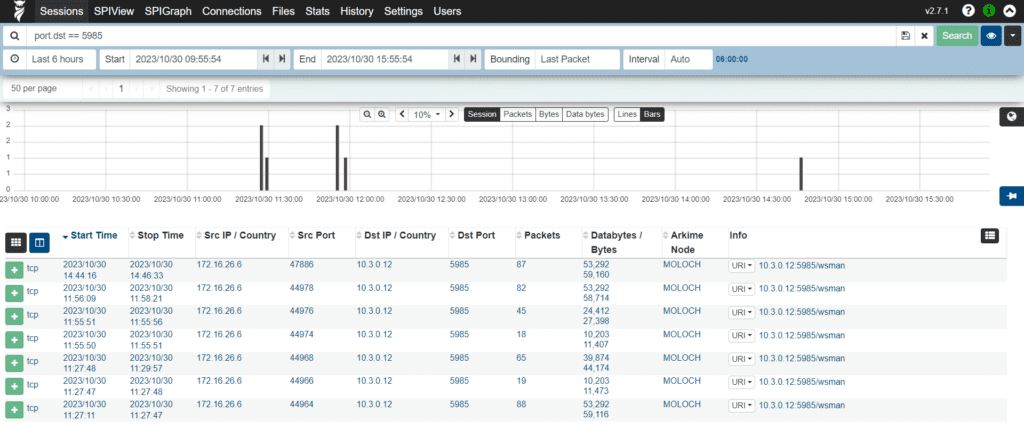
The above finding gives us a clear picture that the external IP is being communicating towards over internal infrastructure over port [5985] with suspicious URL request 5985/wsma
Note: WSMan enables the execution of commands and scripts on remote systems
This unified approach of performing both offensive and defensive operations will typically enhance the organization detection and its investigation, based on our findings and observation we can proceed creating multiple detection rules to further prevent real world adversaries.
Our Offerings:
Premium Edition: Certified Purple Team Analyst V2
Certified Purple Team Analyst V2 [CPTA V2] provides a Unified Approach to Purple Teaming, This training is designed to equip the participants with the knowledge and skills to become an effective Purple Team practitioner.
Community Edition: Purple Teaming Fundamentals
Certified Purple Teaming Fundamentals is the cutting-edge practice that bridges the gap between traditional Red Team (offensive) and Blue Team (defensive) activities. This training is designed to equip the participants with the knowledge and skills to kick-start into purple teaming.