Decoding the Mastery of Cyber Defense: Navigating a Metasploit C2 Incident through Comprehensive Illustrations

OVERVIEW
As we are aware that the evolution of cyber threats is constantly increasing and this particular evolution has tremendously increased the demand of cyber defense over red-team offense, Most often beginners or fresher who might face most confusion to get under the overall working of cyber defense, instead of jumping into various SIEM query or understanding the working of multiple defensive solution its recommend to under how the cyber defense team are been working in an IT environment.
To get a better understanding of its complete working we are illustrating a simple scenario how an enterprise cyber defense team will work coordinatively to handle a particular Metasploit reverse shell incident. As most of us are aware that the Metasploit is simply a C2 which has been incorporated with lots of exploits to compromise a targeted host machine this particular host compromised scenario will often be faced by many organizations. We have been detailing how various different cyber defense teams are working collaboratively to handle one particular revershell activity.
Security Operations
In the overall organization cyber defense the first line of investigation and detection are solely done by the Security Operation Team, where they will be tasked to identify suspicious incidents which have been targeting their internal infrastructure, generally attacks have been either exploited by the external attacker or have been abused by the internal employees. With the help of various cyber defense tools like SIEM, Network Monitoring, EDR , XDR, etc. the SOC can effectively be used to identify and investigate suspicious incidents.

Detection Methodology of SOC
This particular SOC team will monitor the entire Organization for infraction 24 hours a day, 365 days a year, to identify/detect a cyber attack, an organization needs to implement with multiple defensive tools such as SIEM, Network Monitoring, EDR , XDR, etc. these particular tools are handled and managed by SOC analyst. Defensive solutions are often configured with predefined rules to detect cyber attacks, by default many cyber defense solutions are preconfigured with various security rules. In addition, security researchers and engineers are constantly assigned to create multiple detection rules to identify and prevent multiple emerging threats.
Investigation phase
In the investigation phase, SOC Analyst will investigate the alerted incident to determine its true nature. Every alerted incident is manually verified by the security analyst. Afterwards, They will be working collaboratively with various security tools to finalize the nature of the incident. Generally, incidents can be True Positive or False positive, True positives are generally an event which is involved in malicious activity and False positives are the event which have been identified incorrectly by the security solution as a malicious event.
Investigation steps over the detected C2 activity
In case of Metasploit C2, The attacker is constantly engaged in dropping malicious file droppers such as exe, dll, ps1, elf etc. these are mostly identified by the EDR and XDR, based on their working characteristics behavior. In some cases, the attacker might include obfuscation or other techniques to bypass endpoint monitoring. However, if the dropped file tries to communicate with its C2 server, it can be caught with the help of network monitoring tools. Even in some cases the attacker uses HTTPS-based communication, it can be harder for the monitoring tool to detect the suspicious activity, Even if the attacker bypasses the endpoint and network monitoring tools, activities, escalating privileges, pivoting from one machine to another, or creating a scheduled task can be easily caught by the powerful centralized log monitoring tool, SIEM. SIEM is the most powerful tool for monitoring any abnormal change in their normal behavior.
In case of Metasploit C2, Most oftenly the SOC analyst experience the following alerts in their SIEM, EDR, XDR, or Network Monitoring tools:
- Suspicious External network communication detected over port 4444
- Suspicious File execution activity detected
- Privilege escalation activity detected
These alters are further investigated by the analyst to identify the IP addresses, URLs and Hashes associated with suspected incidents and determine their true nature.
Threat Intelligence
After successfully completing the initial investigation, the SOC Analyst will parallelly update the identified true positive information such as {IP, File Name, File Hash, Network and host artifact} in organization threat intel DB. The updated incident details will be further investigated by a threat intel team to determine its impact.

After some time, the threat intel team will start collecting relevant threat feeds associated with the Metasploit agent and droppers. They will also conduct deep hunting to identify any adversary activity associated with them. This information will be used by the threat hunters, while creating their threat hunt hypothese.
Incident Response
In case of post compromise situation the SOC team will further move the particular detected metasploit revershell incident to the Incident Response team, these particular incident responder will sole work to contain and eradicate the particular incident to prevent it from further impact or attack, they will follow a structured Incident Response playbook where they have documented a hierarchical approach what need to done in case of compromised scenarios, the below illustrated is a sample IR play book where its been followed in case of C2 or other malware related activities.
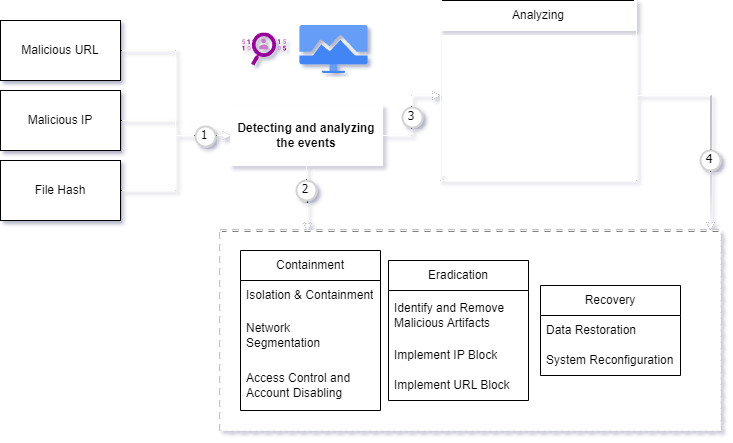
They will also hunt for the identified pattern [IP, URL, File hash] in their organization infrastructure to cross verify that no other host machine in the enterprise is being targeted or get compromised on the same behavior pattern. These IR roles have been considered as a firefighter job everytime they are been tasked with multiple compromise situations which need to be resolved in a short span of time, this IR approach typically reduces the impact of the post compromise attacks.
Threat Hunting
Based on the metasploit revershell findings, the threat hunt team will create multiple hypotheses to be identified and investigated. Below illustrated image gives you a better understanding of how a traditional threat hunt team will work.

In case of these Metasploit revershell the listed are some common hypotheses.
- Abnormal Outbound Network Traffic
- Unusual Process Behavior
- Aberrant System Registry or Configuration Changes
- Anomalous File and Memory Artifacts
The thread hunt team will specifically create a hunt operation to identify a similar pattern of attack which may exist in the organization or not. The advanced stealthier attacks can be easily identified by this threat hunting approach.
Digital Forensics
This particular Digital Forensics team is handled by a group of experts who have very good investigative skills, often post compromise investigations are done by the DFIR team whose sole responsibility is to determine and identify the root cause of the compromised incident. Most often the IR and DFIR team will work often collaboratively when a host has been compromised the IR team will get used to the Containment phase before eradicating the detected malicious artifacts the DFIR team will proceed to acquire the image of the particular compromise machine to determine its root cause.
DFIR proceeds acquiring both Volatile and permanent memory using multiple forensics tools. These acquired image and memory dump will be undergone on various investigations by the analyst such as investigating the process, network communications, Logs/ Histories, Kernel Memory and Objects, Registry, etc.
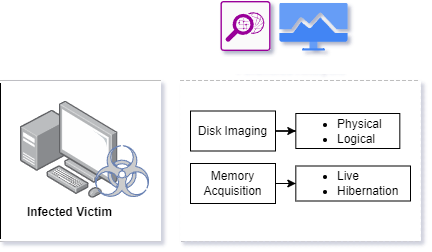
This particular approach helps in understanding the complete attack based on the finding the DFIR team will work collaboratively with SOC to enhance their frontline defense by implementing various detection based on the observed behavior.
Conclusion
In conclusion, the importance of cyber defense in today’s interconnected and technologically driven world cannot be overstated. As our reliance on digital systems and networks continues to grow, so does the threat landscape.
With Blue Team Fundamentals, the team CWL introduces our first-ever blue teaming courses, which is mainly aimed at beginners. This incorporates using efficient research techniques in addition to comprehending how different cyber security teams operate.