Exploring Ticket Injection in Rubeus

When it comes to the AD related operations two famous tools that I can’t possibly overlook are mimikatz and rubeus; Shoutout to Benjamin Delpy and Harmj0y, also many other contributors.
Let’s take a look at a very simple example of retrieving TGT of a user highpriv on domain “CWL.COM” with a tool “Rubeus”. Rubeus accepts the parameter “/ptt” which automatically imports the ticket in the current logon session.Hold on! Did I just mention that “Rubeus imports the ticket into the current logon session”? Light-hearted remarks aside, this knowledge is quite commonplace. However, have you ever wondered what lies beneath the surface of these tools? We will explore this further with Rubeus.
Asking for TGT for highpriv user with its aes256 key and commanding Rubues to import the retrieved ticket.

Once the TGT for the highpriv is imported one can request access to the services in the network, here we’re requesting cifs service in dc01 machine.
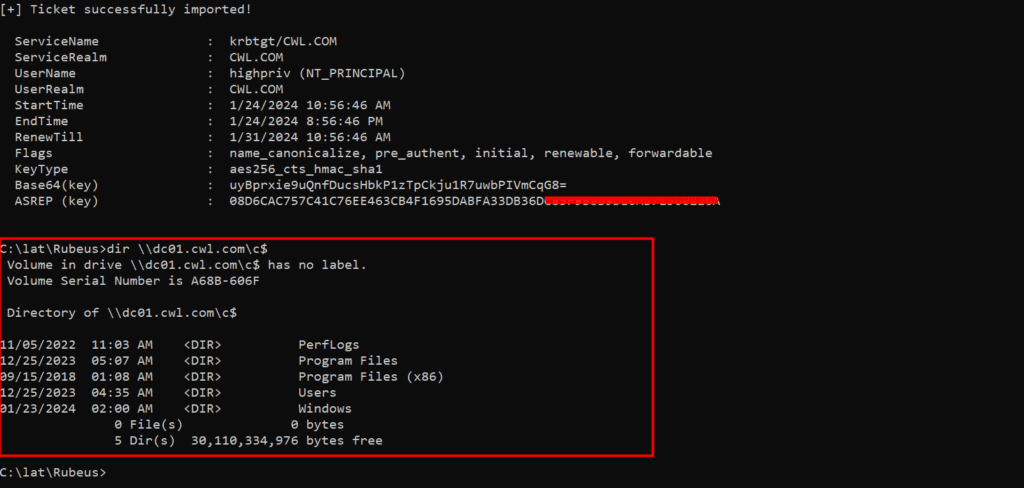
Rubeus: Import Ticket
Since we’re only interested in the ticket injection part, we’ll make an assumption that Rubues has already received the TGT of the above-mentioned user and is about to import the ticket into the current session. We’ll further dig inside the function ImportTicket.

Here, first it’ll try to open the connection handle to LSA based on the privileges that we have. For us it’s opening the connection handle to the LSA with LsaConnectUntrusted API.
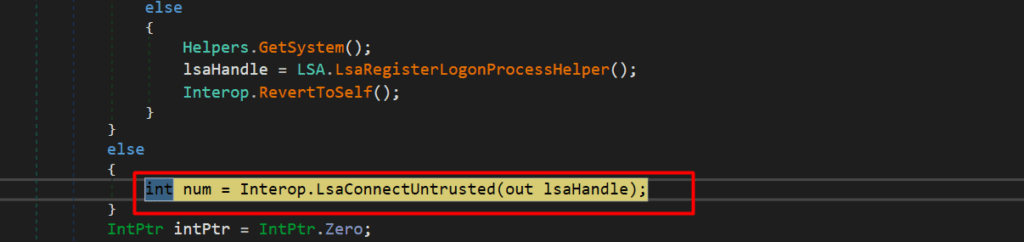
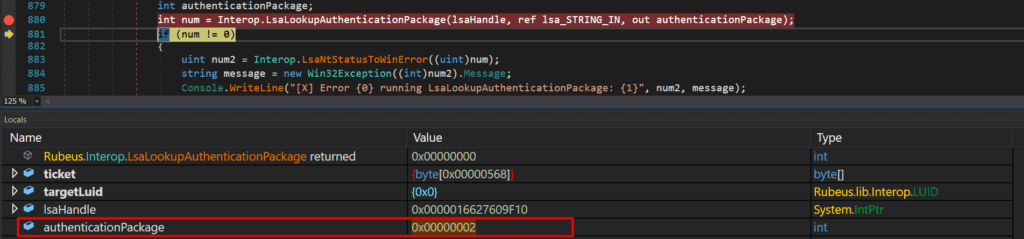
Then the handle is passed into the API LsaLookupAuthenticationPackage along with string “kerberos” where it’s expecting an authentication package identifier as an output.

We can verify the above mentioned details in the following function definition from the microsoft documentation.
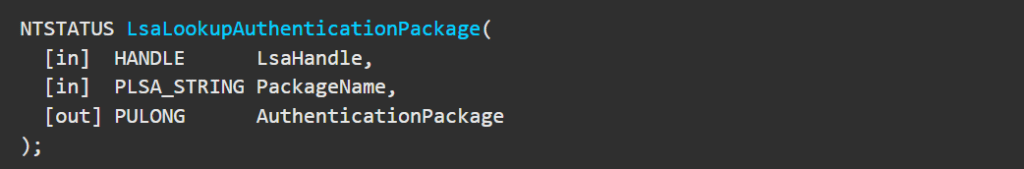
The Authenticator Package identifier value that it outputs is 0x00000002;
Then the KERB_SUBMIT_TKT_REQUEST structure is filled with the following details. One important member to note here is the message type i.e. KerbSubmitTicketMessage.

We can also view the TGT in memory.

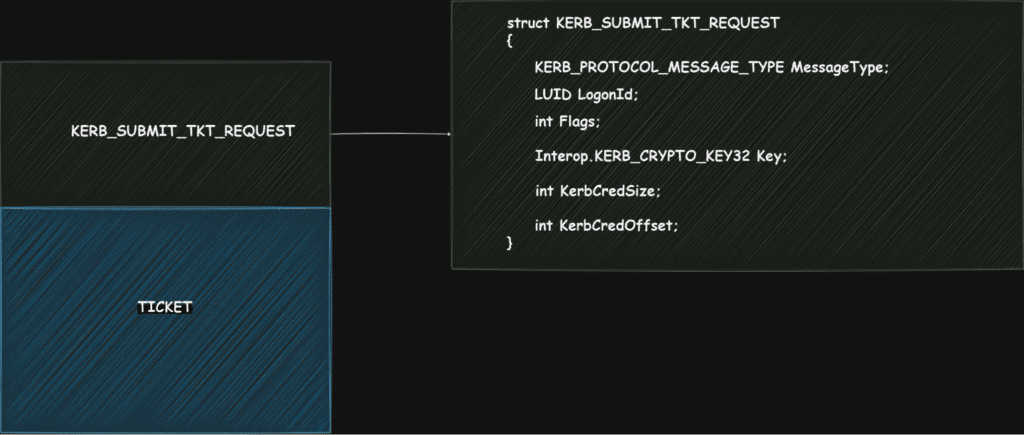
KERB_SUBMIT_TKT_REQUEST structure + TGT
Once the buffer is crafted (KERB_SUBMIT_TKT_REQUEST structure + TGT ) it’ll feed inside the LsaCallAuthenticationPackage along with LSA handle and authentication package identifier which is retrieved from LsaLookupAuthenticationPackage.
If you recall the message type above i.e. KerbSubmitTicketMessage; this message type is one of the switches to trigger one of the dispatch routines inside LsaCallAuthenticationPackage. And this routine basically updates the ticket cache. And this is how the ticket ends up in our command session as well.

Hold on a moment! Are you feeling completely satisfied after reading this blog? Well, I wasn’t, and here’s the exciting part – the other half of this blog is still in the wings, waiting to be unleashed!
Join Enterprise Lateral Movement Specialist [CELMS] course launch webinar on January 26, 2024, from 8-9 PM IST. Enrolled participants will receive:
- Webinar recording
- Downloadable PPT
- An attendance certificate
- Additionally, 5 lucky winners stand a chance to get FREE access
- 10% OFF discount for the Enterprise Lateral Movement Specialist [CELMS] course.
This comprehensive course includes recorded videos, engaging exercises, and technical support. Successfully completing the on-demand exam earns you a CWL verified accredible badge, enhancing your professional profile. Don’t miss out on this opportunity!
Author: Mr. John Sherchan, Red Team Security Researcher at CyberWarFare Labs
Proof-read by: Mr. Yash Bharadwaj, CTO at CyberWarFare Labs